Avanan Report: Business Email Compromise Scam Leads Credential Harvesting Evernote Page
- Written by Jeremy Fuchs, Cybersecurity Researcher/Analyst at Avanan, A Check Point Software Company

Business Email Compromise attacks are one of the fastest-growing and most difficult-to-stop attacks in the cybersecurity space. There are a number of variants, but in general, these attacks spoof someone in your organisation, often an executive, and don’t use any malware or malicious links. (Some BEC attacks do use malware or malicious links, but the toughest ones to stop are primarily text-based.)
These attacks have led to significant financial losses, primarily because they seem real. Think about it from an end-user perspective. If you get an email from your “CEO” asking you to pay an invoice, or worse money to a customer, do you say no? That’s what hackers are hoping for.
In this BEC attack, we’ve seen hackers get even more creative.
In this attack brief, researchers at Avanan, a Check Point Software Company, will discuss how threat actors are using the legitimacy of Evernote to help make their BEC attacks even more convincing.
Attack
In this attack, hackers are using Evernote links to host invoices that are sent in Business Email Compromise attacks
- Vector: Email
- Type: Phishing
- Techniques: Business Email Compromise
- Target: Any end-user
Email Example #1
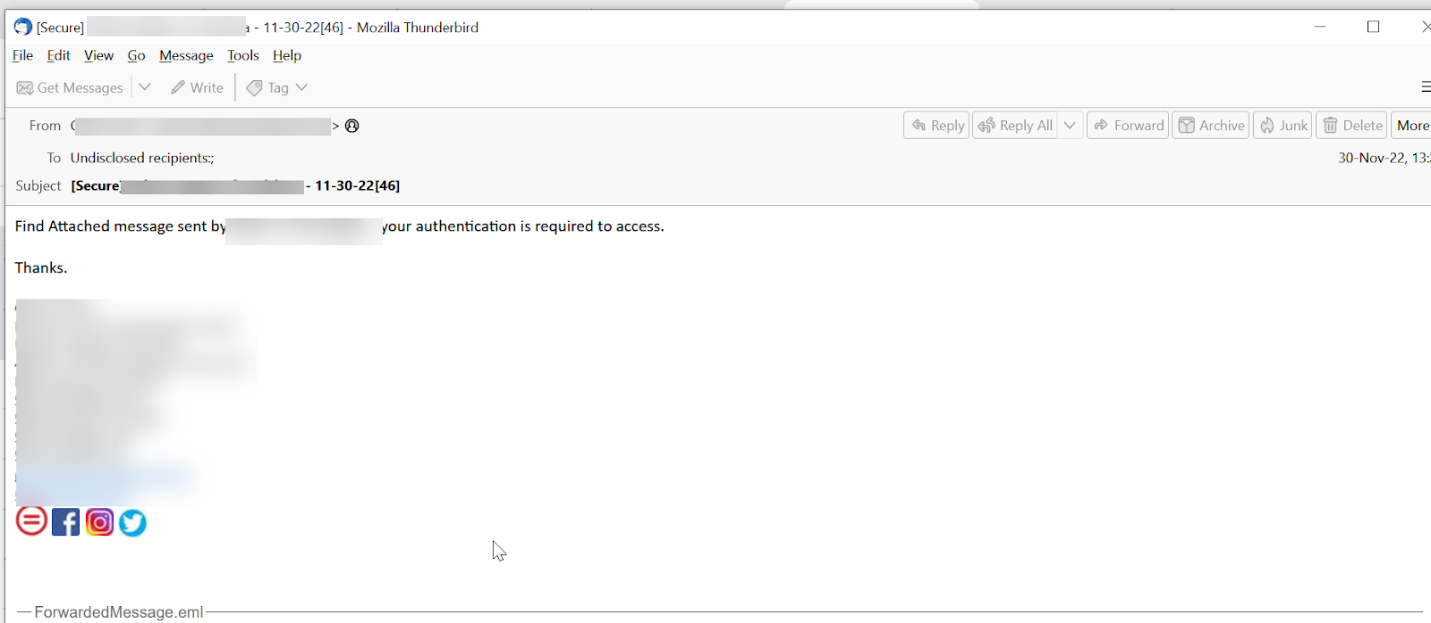
This starts as an attached message, sent directly from the President of the organisation in question. This is a compromised account. Hackers will often spoof executives using trickery in the sender field; in this case, the president of the organisation was actually compromised, and thus is sent directly from that person’s account.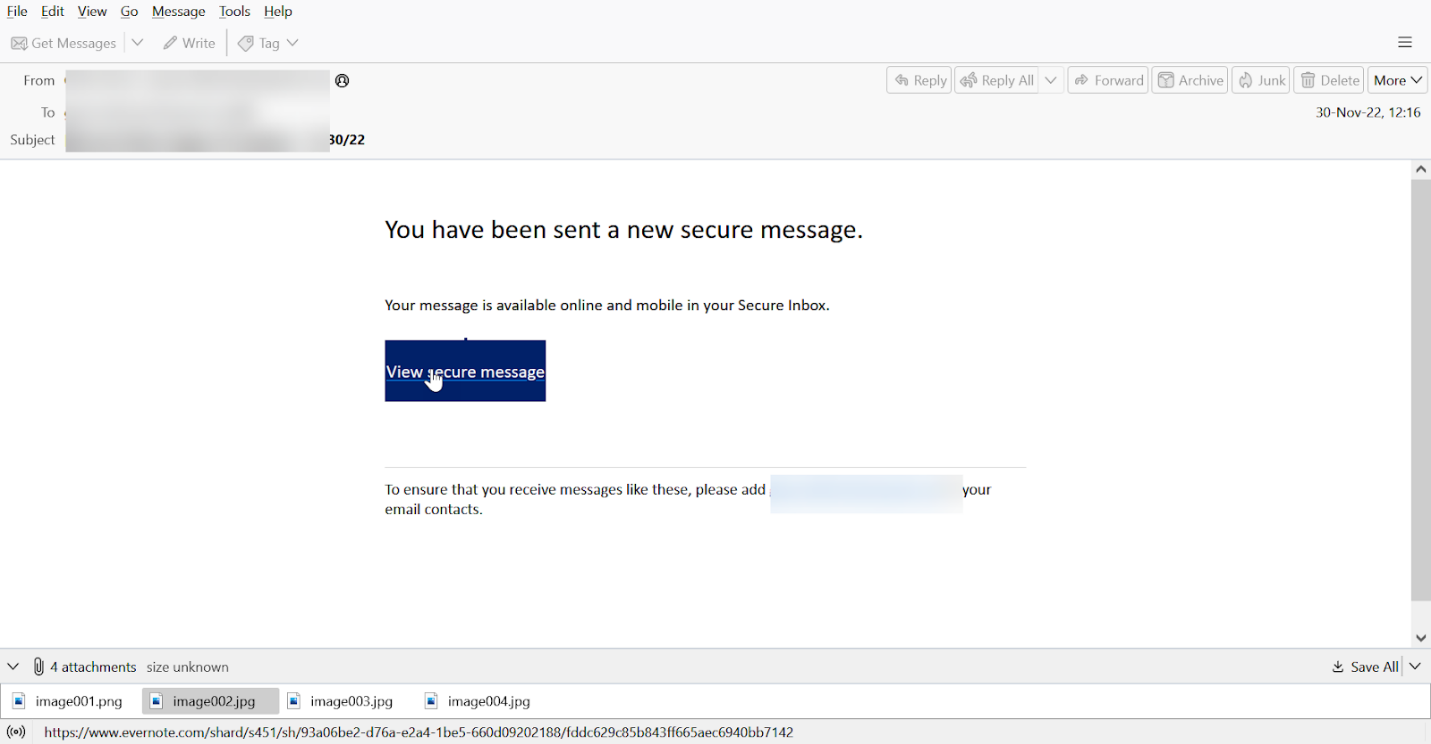
The attached message leads to an email saying there’s a “secure message.’ The link goes to an Evernote page.
The Evernote page has since been taken down. But Evernote, like many legitimate websites, is being increasingly used for hacking. Recently, according to Huntress, there’s been an uptick in hosting malicious documents on Evernote.
In this case, there’s a document on Evernote that leads to a fake login page to steal credentials.
Techniques
Business Email Compromise attacks are tough to stop from a security perspective, and tough to recognise from an end-user perspective. This attack is a hallmark of that difficulty.
It starts with an email from the President of an organisation. The account was compromised, so the email will pass all authentication measures. The message itself is not malicious. It links to a document in Evernote–not a malicious site.
From a security perspective, this looks clean. If you’re an end-user, it looks clean. Using a legitimate site like Evernote–particuarly if Evernote is already used in that organisation–adds a ton of credence.
In short, it’s an incredibly well-crafted attack.
Stopping BEC attacks, then, become incredibly important, and there are a few things that need to be done. For one, AI and ML need to be involved. There needs to be the ability to understand the content of an email, the context and the tone, and understanding when that differs. For example, does the President of the organisation typically send links to Evernote?
From there, the organisation has to be able to re-write and detect malicious links and attachments. Evernote is not malicious; the document included is. Can the security service follow that link and attachment all the way through, understanding if it is indeed malicious?
And, does the organisation have account takeover protection? We don’t know how this user was initially compromised, but today’s world provides the hacker plenty of ways to do it–email, text, voice, chat, file-sharing. Understanding login events, configuration changes and end-user activities throughout the entire productivity suite is key.
Best Practices: Guidance and Recommendations
To guard against these attacks, security professionals can do the following:
- Create processes for employees to follow when paying invoices or entering credentials
- Implement advanced security that looks at more than one indicator to determine in an email is clean or not
- Utilise malicious URL detection and rewriting to follow the link to its intended destination in a safe manner







